
Ransomware Protection
Monitor traffic to your IBM i through exit point connections like FTP telnet and ODBC, as well as socket layer access.
Ready to wrangle IBM i modernization? Fresche is riding into Fort Worth for POWERUp & we can’t wait to meet you. Visit us at booth #109!
Business-critical data on IBM i is not immune to ransomware, cybercrimes, and data theft. Key areas of exposure include the files and directories in your IFS and network connectivity such as ODBC, FTP, web server applications, and other socket connections. Use the Fresche Security Suite to increase governance and compliance, mitigate risk, and deliver greater operational efficiency.
Monitor traffic to your IBM i through exit point connections like FTP telnet and ODBC, as well as socket layer access.
Lock down, monitor, and get real-time notifications about your exit points and access pre-defined security compliance reports.
Easily ensure compliance with industry standards and streamline auditing processes for enhanced regulatory adherence.
Encrypt, mask, and scramble field values so you can protect your data and comply with security regulations such as PCI and HIPAA. Get real-time alerts when sensitive data is accessed.
Identify the right data to analyze and get alerts to security incidents as they occur to stop intrusions and minimize internal and external threats.
Implement an extra layer of security on user account access by requiring token entry in addition to passwords.
Learn about critical vulnerabilities to look for on IBM i systems caused by misconfigurations and effective, automated ways to remediate them.
Watch NowUniquely created for IBM i, the Fresche Security Suite provides complete system monitoring capabilities to quickly uncover malware, malicious code, and potential threats. Designed for ease of use, the software comes with a modern intuitive dashboard that provides real-time alerts, allowing you to deal with internal and external threats proactively.
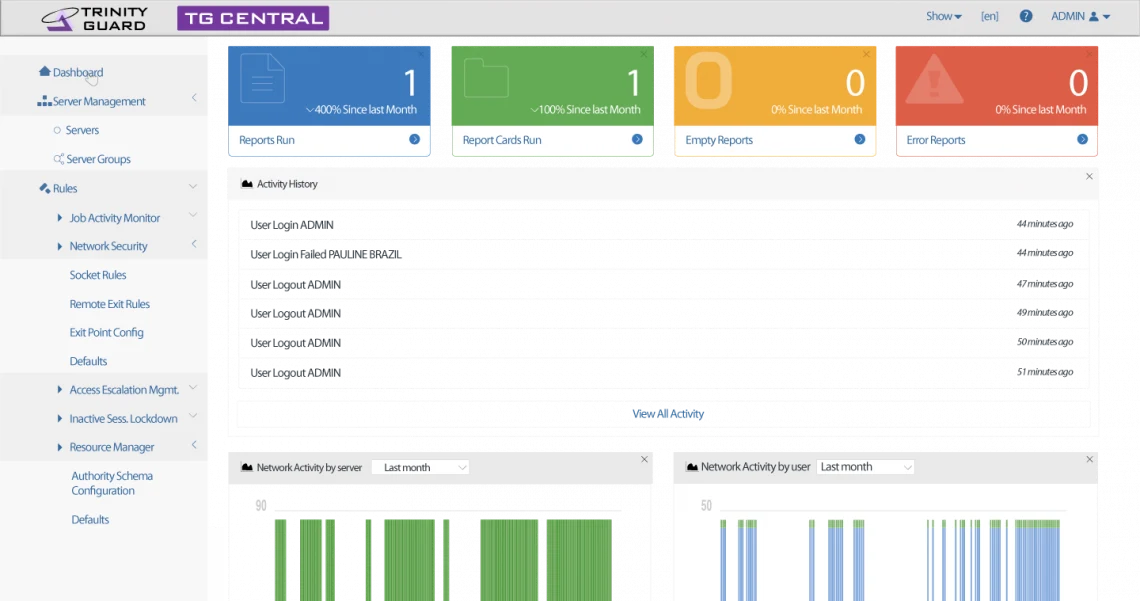
Monitor security in complex environments and configure privilege escalation & network security from a single web-based console.

Safeguard the business-critical assets stored on your IBM i with user profile management, access escalation management and inactive session lockdown.
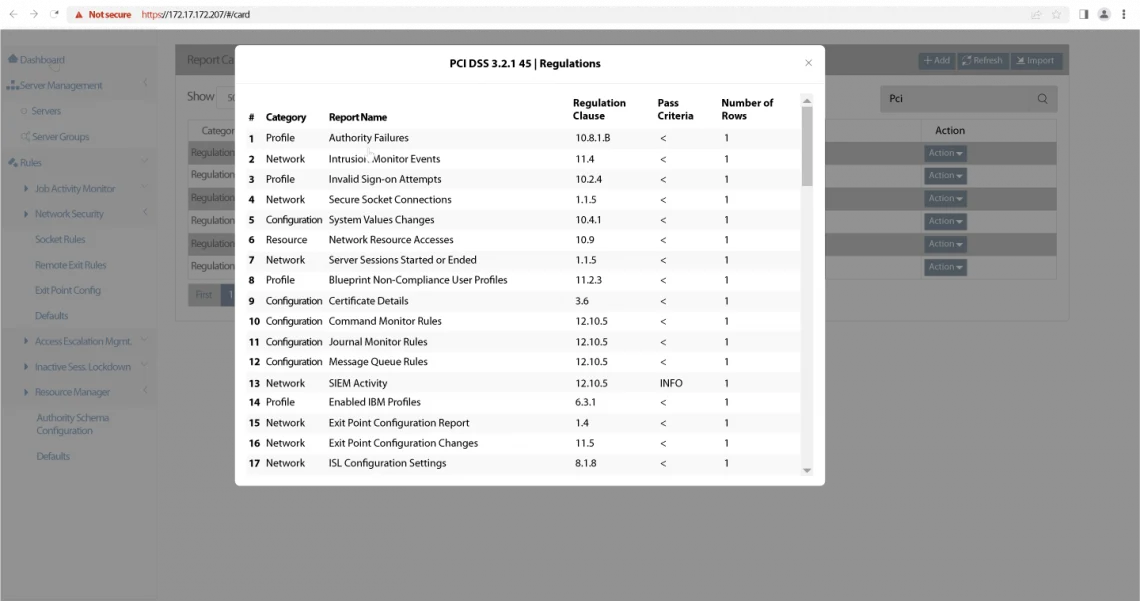
Meet internal and external audit requirements and regulatory compliance mandates by simplifying data collection with robust reporting and flexible output.

Get real-time alerts that alert you to potentially suspicious system activity so you can quickly take action and protect your systems.

Go beyond data encryption and provide an additional protection layer by masking and scrambling data that is visible to users.

Quickly strengthen user authentication security for users who are signing into your organization’s IBM i systems.
billed annually/ LPAR
What’s included:
Flexible Terms
Fresche Security is also available via flexible one-time or unlimited licensing models for enterprises.
Work with experienced security professionals who identify vulnerabilities, prioritize fixes, and help improve your security position.
Security AssessmentStarting as low as $0 Security Strategy ConsultingSpeak with an expert Security Consulting20 hours at $5000 (expert services bundle) Penetration Testing$5,750/ LPARKnow where you stand by performing an IBM i security audit with the Fresche TGSecurity Suite. With just a few clicks, evaluate 47 critical points and access the results in a clear and concise pass/fail format.